Use case
Secure Azure Infrastructure Redesign with Private Networking
- Zinka Desai
About the Customer
Skyhaul Logistics is an innovative online platform transforming air cargo logistics for small and medium businesses (SMBs) in emerging markets. It offers real-time air freight rates and a seamless booking experience, significantly reducing logistical complexities and operational costs. Skyhaul Logistics empowers SMBs to access reliable, timely air shipments and scale their logistics operations efficiently.
Customer Challenge
As Skyhaul Logistics scaled its operations, their existing Azure infrastructure presented serious security and operational risks. The architecture was fully public-facing, leaving critical services—such as Azure PostgreSQL databases and Azure App Services—exposed to unrestricted internet access. This lack of isolation and control introduced the following key issues:
- Unrestricted Public Access: Core services were accessible from the internet, increasing the attack surface and vulnerability to breaches.
- No Network Segmentation: The absence of dedicated virtual networks created a flat network topology, increasing the risk of lateral movement during security incidents.
- Limited Traffic Control: Without structured ingress filtering or traffic inspection, the system remained susceptible to unauthorized access and malicious payloads.
The challenge was to completely re-architect the infrastructure to prioritize security, scalability, and efficient operations, while maintaining ease of use for administrative teams.
Solution
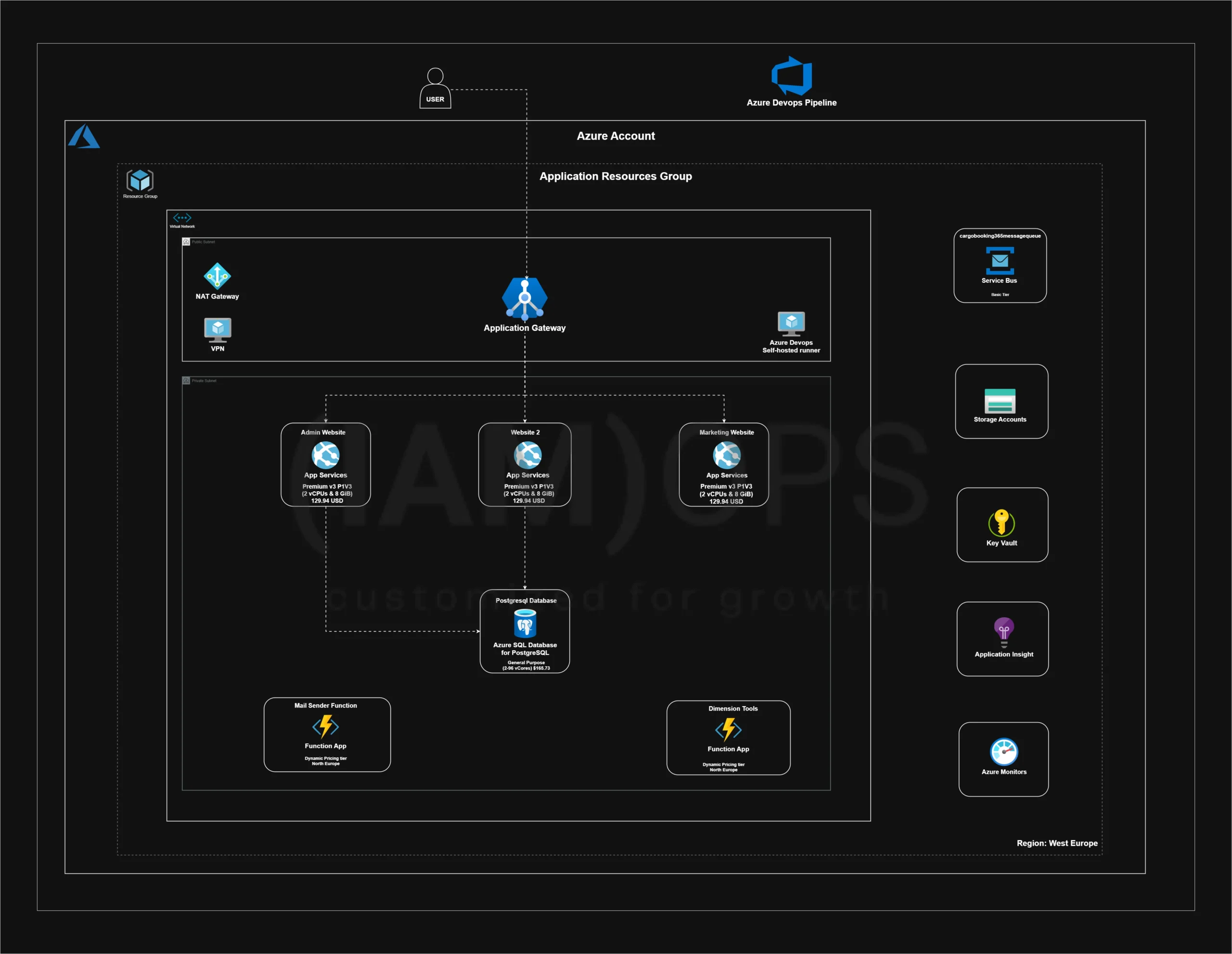
IAMOPS designed and implemented a secure and scalable Azure infrastructure aligned with modern DevOps practices. The solution included:
- Private Subnets: Core services like Azure PostgreSQL and Azure App Services were deployed into private subnets, removing them from direct public access.
- Application Gateway: An Azure Application Gateway was deployed to handle SSL termination, enforce Web Application Firewall (WAF) rules, and distribute load.
- VPN Deployment: A VPN gateway ensured that administrative access to the database was available only through a secure, encrypted tunnel.
- Network Segmentation: Virtual networks and subnets were carefully segmented to isolate public-facing components from private infrastructure.
- Advanced Monitoring and Access Control: Azure Monitor, Application Insights, Azure Active Directory (AAD), and Role-Based Access Control (RBAC) were configured for visibility, compliance, and identity governance.
Additional security practices included using Azure Key Vault for secret management, implementing Transparent Data Encryption (TDE) on databases, and enforcing least-privilege access with RBAC. Automation was achieved via Azure DevOps pipelines for CI/CD, including self-hosted runners to deploy securely to private resources.
Results & Benefits
The project delivered significant security, operational, and business benefits:
- Enhanced Security Posture: The complete isolation of critical services and the use of VPN, RBAC, and TDE led to a dramatically reduced attack surface and improved data protection.
- Operational Efficiency: Automation through Azure DevOps and resource grouping via Azure Resource Groups streamlined operations and reduced manual overhead.
- Scalability and Resilience: The redesigned architecture supports traffic spikes through load-balanced gateways and ensures resilience with proactive monitoring tools.
- Quantifiable Improvements:
- Eliminated public exposure of databases and core services.
- Reduced likelihood of data breaches through encrypted data and secrets.
- Improved performance and reliability through structured traffic management and monitoring.
TCO Analysis
- Initial Setup Costs:
- Engineering hours invested in defining infrastructure as code (IaC).
- Configuration of CI/CD pipelines and self-hosted runners.
- Ongoing Operational Costs:
- Azure services: App Services, Application Gateway, Networking, VPN.
- Maintenance of pipelines and deployment workflows.
- Cost Efficiency: By reducing potential security incidents and automating infrastructure tasks, the solution reduced long-term risk-related costs.
Learning and Best Practices
This project emphasized the need for comprehensive security in cloud-native environments. Key takeaways include:
- Isolate Critical Resources using private subnets.
- Control Traffic via Application Gateway with WAF.
- Secure Administrative Access using VPN and MFA.
- Automate Everything using Azure DevOps and Key Vault.
- Enforce Identity Governance using RBAC and least privilege principles.
These practices collectively enabled Skyhaul Logistics to meet enterprise-level security and operational standards.
About IAMOPS
IAMOPS is a full DevOps suite company that supports technology companies to achieve intense production readiness.
Our mission is to ensure that our clients’ infrastructure and CI/CD pipelines are scalable, mitigate failure points, optimize performance, ensure uptime, and minimize costs.
Our DevOps suite includes DevOps Core, NOC 24/7, FinOps, QA Automation, and DevSecOps to accelerate overall exponential growth.
As an AWS Advanced Tier Partner and Reseller, we focus on two key pillars: Professionalism by adhering to best practices and utilizing advanced technologies, Customer Experience with responsiveness, availability, clear project management, and transparency to provide an exceptional experience for our clients.

